

In the rapidly evolving realm of cryptocurrencies, safeguarding your digital wealth is a top priority. The options are as varied as the tokens themselves, and each choice comes with its own set of advantages and risks. While exchanges, software wallets, and hardware wallets are all contenders, the ultimate goal is to keep your crypto safe and sound. Let’s explore the current options for your crypto storage and understand why hardware wallets are emerging as the top pick for the security-conscious.
Many people who are into cryptocurrencies tend to start by keeping their digital assets on cryptocurrency exchanges. These platforms, like Coinbase, Binance, and CoinSpot, make it easy to manage and trade your assets quickly. However, they also come with significant security risks.

The problem with exchanges is that they are centralized, which means they are attractive targets for cybercriminals. Despite their efforts to have strong security measures, they can still be vulnerable to attacks. When you keep your cryptocurrency on an exchange, you don’t have full control over your private keys, which are like the keys to your financial safety.
This is why it’s highly recommended to always move your cryptocurrency from the exchange to a wallet to keep your money safe. By doing this, even if the exchange gets hacked, goes out of business, or faces unexpected problems, you won’t lose the cryptocurrency you’ve worked hard to accumulate.
Software wallets, available as mobile apps or desktop programs, offer users more control over their cryptocurrency compared to exchanges. However, they come with their share of risks, primarily due to their “hot” nature. This means they are always connected to the internet, which poses a significant threat to your crypto security.
To safeguard your crypto, it’s crucial to avoid storing your private keys and funds in hot wallets like Metamask. Instead, opt for cold storage solutions such as hardware wallets.
Hardware wallets are specialized devices designed for the secure storage of cryptocurrencies. They remain offline, isolated from the internet, and safeguard your assets by storing private keys securely. Unlike software wallets, hardware wallets never expose private keys to the online world, making them immune to remote hacks.
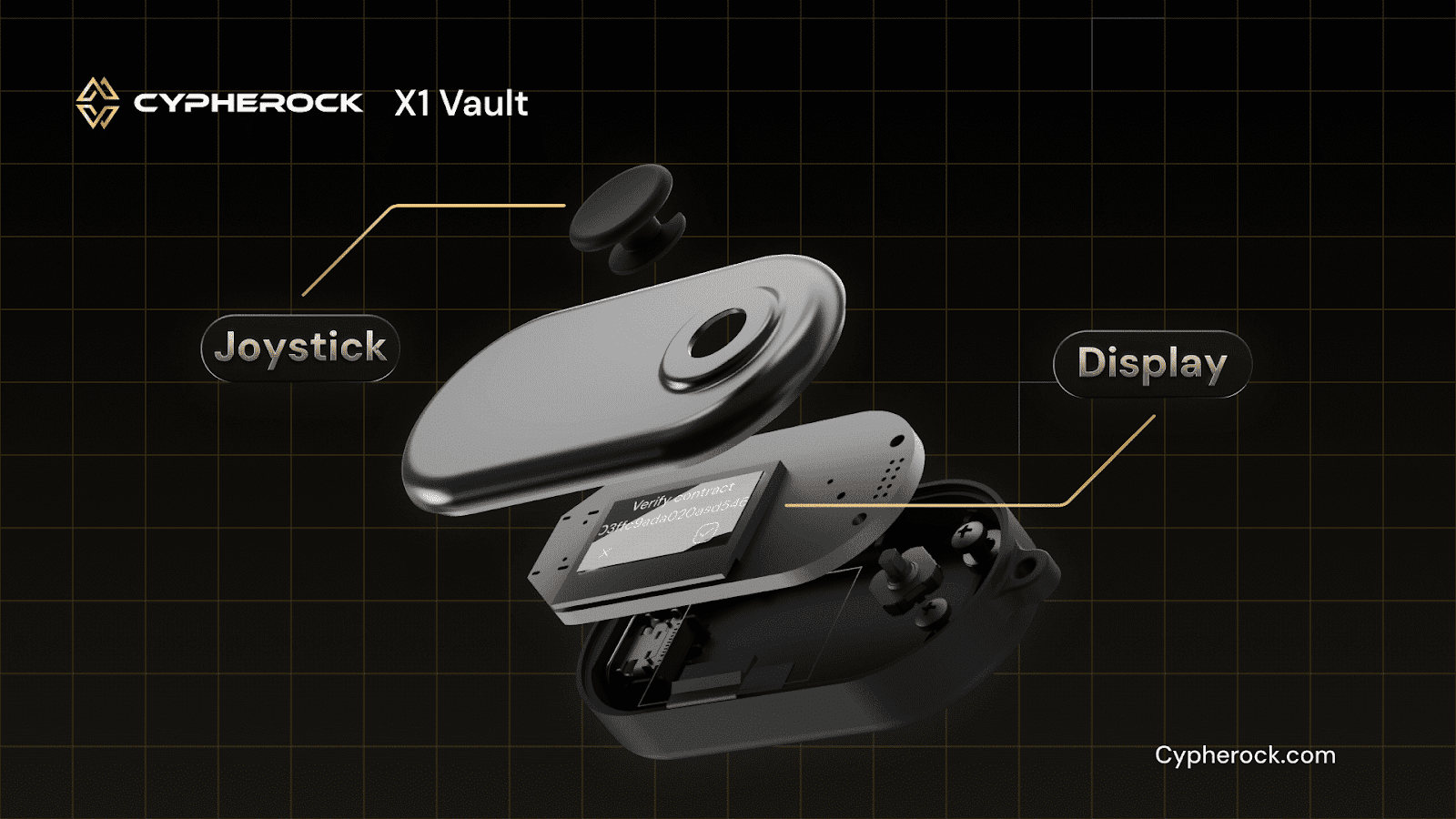
For instance, the Cypherock X1 goes beyond traditional hardware wallets by decentralizing private keys using Shamir Secret Sharing. This ensures that even if one component is lost, the user retains access to their funds using the remaining parts.
Hardware wallets are the pinnacle of crypto security. By isolating private keys and offering robust features, they address the key vulnerabilities associated with exchanges and software wallets. Make the informed choice to safeguard your digital wealth.
We are live for orders @ www.cypherock.com/product/cypherock-x1
Connect with us:
Twitter: twitter.com/CypherockWallet
Telegram: t.me/cypherock
